17+ pages list and describe the criteria for selecting information security personnel 1.8mb. Management of Information Security 5th Edition Edit edition This problem has been solved. 98 837 Review List and describe the criteria for selecting InfoSec personnel. The objective of the Personnel Security Program is to make a reasonable determination that individuals granted access to classified information or assigned to sensitive positions are and will remain loyal trustworthy and reliable. Check also: describe and learn more manual guide in list and describe the criteria for selecting information security personnel Security should be reviewed.
3To provide the students the best possible education and describe the students level of performance 4To monitor the progress of students based on the goals set 5To motivate students to learn and the teachers to be able to. In scenario of selecting a security officer for Australian Tax Office to manage and backup all databases name some of criteria this employee should comply with.

Understanding Information Assets Understanding Each Step
| Title: Understanding Information Assets Understanding Each Step |
| Format: eBook |
| Number of Pages: 284 pages List And Describe The Criteria For Selecting Information Security Personnel |
| Publication Date: April 2020 |
| File Size: 1.2mb |
| Read Understanding Information Assets Understanding Each Step |
 |
What are some of the factors that influence an organizations hiring decisions.
List and describe the criteria used to determine whether an actual incident is occurring. Staffing The Security Function Selecting information security personnel is based on a number of criteria including the principles of supply and demand. Rationale This assessment item is designed to test your understanding of ICT management and information security topics issues and be able to. Experience credentials hiring issues and background checks. It is necessary to have a thorough understanding of its origins and processes. Describe the types of services offered by brokerage firms and discuss the criteria for selecting a.

Guiding Principles In Information Security Infosec Resources
| Title: Guiding Principles In Information Security Infosec Resources |
| Format: PDF |
| Number of Pages: 183 pages List And Describe The Criteria For Selecting Information Security Personnel |
| Publication Date: August 2020 |
| File Size: 5mb |
| Read Guiding Principles In Information Security Infosec Resources |
 |

Cyber Security Goals Javatpoint
| Title: Cyber Security Goals Javatpoint |
| Format: PDF |
| Number of Pages: 160 pages List And Describe The Criteria For Selecting Information Security Personnel |
| Publication Date: August 2017 |
| File Size: 2.1mb |
| Read Cyber Security Goals Javatpoint |
 |
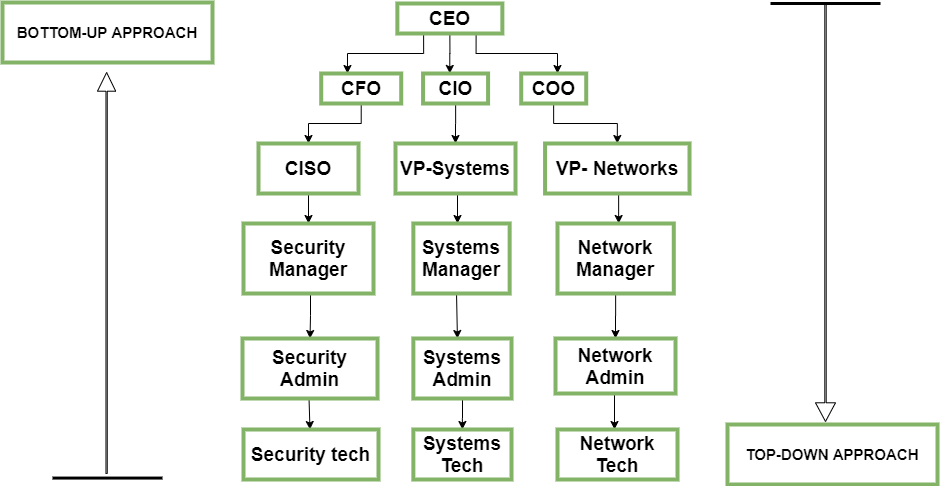
Approaches To Information Security Implementation Geeksfeeks
| Title: Approaches To Information Security Implementation Geeksfeeks |
| Format: eBook |
| Number of Pages: 312 pages List And Describe The Criteria For Selecting Information Security Personnel |
| Publication Date: January 2018 |
| File Size: 1.5mb |
| Read Approaches To Information Security Implementation Geeksfeeks |
 |

The 3 Types Of Security Controls Expert Explains Purplesec
| Title: The 3 Types Of Security Controls Expert Explains Purplesec |
| Format: PDF |
| Number of Pages: 225 pages List And Describe The Criteria For Selecting Information Security Personnel |
| Publication Date: February 2019 |
| File Size: 1.5mb |
| Read The 3 Types Of Security Controls Expert Explains Purplesec |
 |
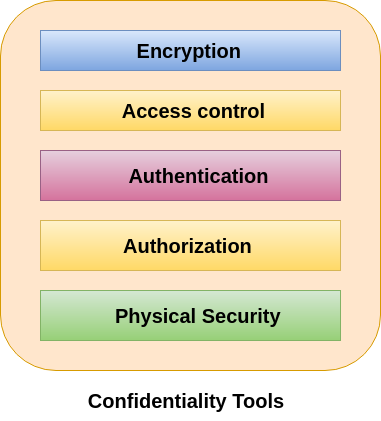
Cyber Security Goals Javatpoint
| Title: Cyber Security Goals Javatpoint |
| Format: PDF |
| Number of Pages: 170 pages List And Describe The Criteria For Selecting Information Security Personnel |
| Publication Date: March 2018 |
| File Size: 5mb |
| Read Cyber Security Goals Javatpoint |
 |

The Chief Information Security Officer Ciso Role Explained Bmc Software Blogs
| Title: The Chief Information Security Officer Ciso Role Explained Bmc Software Blogs |
| Format: PDF |
| Number of Pages: 266 pages List And Describe The Criteria For Selecting Information Security Personnel |
| Publication Date: February 2017 |
| File Size: 1.35mb |
| Read The Chief Information Security Officer Ciso Role Explained Bmc Software Blogs |
 |

What Is An Information Security Policy Upguard
| Title: What Is An Information Security Policy Upguard |
| Format: eBook |
| Number of Pages: 299 pages List And Describe The Criteria For Selecting Information Security Personnel |
| Publication Date: December 2019 |
| File Size: 1.6mb |
| Read What Is An Information Security Policy Upguard |
 |

Enterprise Information Security Program It Security Policy Office
| Title: Enterprise Information Security Program It Security Policy Office |
| Format: PDF |
| Number of Pages: 163 pages List And Describe The Criteria For Selecting Information Security Personnel |
| Publication Date: January 2021 |
| File Size: 2.6mb |
| Read Enterprise Information Security Program It Security Policy Office |
 |

2 3 Security Governance Ponents Understanding Information Security Governance Informit
| Title: 2 3 Security Governance Ponents Understanding Information Security Governance Informit |
| Format: eBook |
| Number of Pages: 231 pages List And Describe The Criteria For Selecting Information Security Personnel |
| Publication Date: December 2019 |
| File Size: 1.1mb |
| Read 2 3 Security Governance Ponents Understanding Information Security Governance Informit |
 |

Top 10 It Security Actions 6 Provide Tailored Cyber Security Training Itsm 10 093 Canadian Centre For Cyber Security
| Title: Top 10 It Security Actions 6 Provide Tailored Cyber Security Training Itsm 10 093 Canadian Centre For Cyber Security |
| Format: eBook |
| Number of Pages: 137 pages List And Describe The Criteria For Selecting Information Security Personnel |
| Publication Date: February 2020 |
| File Size: 1.2mb |
| Read Top 10 It Security Actions 6 Provide Tailored Cyber Security Training Itsm 10 093 Canadian Centre For Cyber Security |
 |
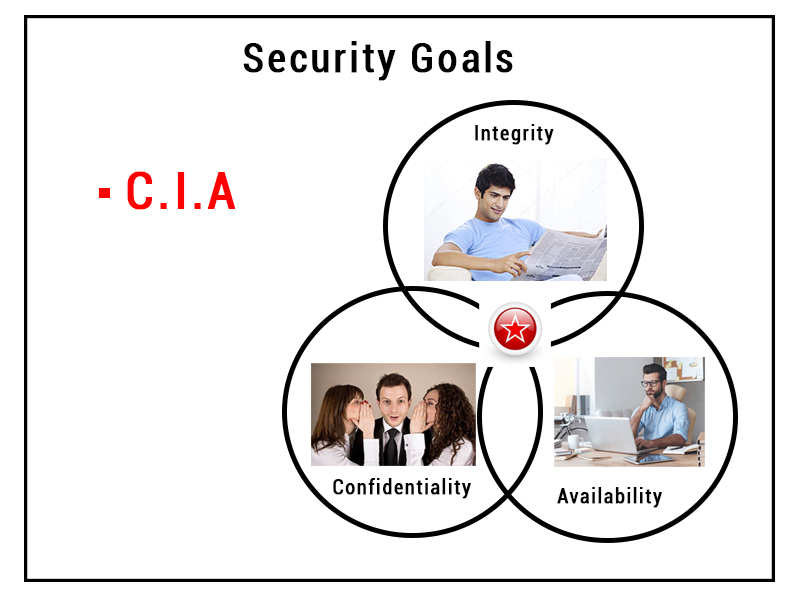
The Cia Triad Confidentiality Integrity Availability Panmore Institute
| Title: The Cia Triad Confidentiality Integrity Availability Panmore Institute |
| Format: ePub Book |
| Number of Pages: 129 pages List And Describe The Criteria For Selecting Information Security Personnel |
| Publication Date: October 2017 |
| File Size: 3.4mb |
| Read The Cia Triad Confidentiality Integrity Availability Panmore Institute |
 |
List and describe the criteria for selecting InfoSec personnel. Through the course of their daily activities they have access to the keys of the kingdom Network security engineers have access to systems that collect network traffic system security engineers can manipulate access to data on systems and penetration test engineers know the vulnerabilities and weaknesses to critical corporate systems. What are the critical issues that management must consider when dismissing an employee.
Here is all you have to to learn about list and describe the criteria for selecting information security personnel View Homework Help - Chapter 11 from CS 440 at Saint Mary-of-the-Woods College. Experience credentials hiring issues and background checks. Through the course of their daily activities they have access to the keys of the kingdom Network security engineers have access to systems that collect network traffic system security engineers can manipulate access to data on systems and penetration test engineers know the vulnerabilities and weaknesses to critical corporate systems. Top 10 it security actions 6 provide tailored cyber security training itsm 10 093 canadian centre for cyber security enterprise information security program it security policy office understanding information assets understanding each step cyber security goals javatpoint what is an information security policy upguard the 3 types of security controls expert explains purplesec It is necessary to have a thorough understanding of its origins and processes.